White Papers or Reports on RFID
RFID Technologies and Solutions
 Counterfeit Prevention with Properly Configured RFID tags. In the year 2000, the World Health Organization estimated that more than 7% of the world’s pharmaceuticals were counterfeit. In the United States alone, the loss to counterfeit drugs was estimated to be in the range of $2 billion. By 2005, the estima….[5/29/2005]
Counterfeit Prevention with Properly Configured RFID tags. In the year 2000, the World Health Organization estimated that more than 7% of the world’s pharmaceuticals were counterfeit. In the United States alone, the loss to counterfeit drugs was estimated to be in the range of $2 billion. By 2005, the estima….[5/29/2005] White Paper on Cargo Container Security [5/5/2005]
White Paper on Cargo Container Security [5/5/2005] AVANTE to License and Deploy its RFID Cargo Seal to Secure Container Shipping. AVANTE has developed the long-sought solution of intrusion detection by placing active tags (ZONER™) inside the container. ZONER™ differs from traditional tags by emitting a burst of 433 MHz signals at several discrete power levels every few seconds. An….[4/6/2005]
AVANTE to License and Deploy its RFID Cargo Seal to Secure Container Shipping. AVANTE has developed the long-sought solution of intrusion detection by placing active tags (ZONER™) inside the container. ZONER™ differs from traditional tags by emitting a burst of 433 MHz signals at several discrete power levels every few seconds. An….[4/6/2005] Smart-Portal.RFID conveyer portal antenna for bag sortation, RFID dock and conveyer portal for containers and pallets [4/12/2004]
Smart-Portal.RFID conveyer portal antenna for bag sortation, RFID dock and conveyer portal for containers and pallets [4/12/2004] IATA RFID Tag. IATA format RFID tag with 45mm width and 4 ft read distance: soldered “strap” on copper inlay for reliability. Pedigree data usage is illustrated. [4/12/2004]
IATA RFID Tag. IATA format RFID tag with 45mm width and 4 ft read distance: soldered “strap” on copper inlay for reliability. Pedigree data usage is illustrated. [4/12/2004] RFID ID Tag. RFID tag with staff and passengers for access control and audit for extra security [4/12/2004]
RFID ID Tag. RFID tag with staff and passengers for access control and audit for extra security [4/12/2004] Positive Passenger and Bag Matching. Point-of-loading matching eliminates errors and improves security. [4/12/2004]
Positive Passenger and Bag Matching. Point-of-loading matching eliminates errors and improves security. [4/12/2004] Data Authenticity. “Relational Check Code” authenticates data on RFID tag to provide extra security for airlines and passengers [4/12/2004]
Data Authenticity. “Relational Check Code” authenticates data on RFID tag to provide extra security for airlines and passengers [4/12/2004] Is 13.56 MHz RFID technology equally or more effective than 125 KHz for livestock identification and tracking? We believe the flexible appropriate approach taken by USAIP can benefit from the fast development of RFID technology in the supply chain market place. Based on the goals and the implementation phases expected of this plan, we believe that 13.56 MHz ba….[1/10/2004]
Is 13.56 MHz RFID technology equally or more effective than 125 KHz for livestock identification and tracking? We believe the flexible appropriate approach taken by USAIP can benefit from the fast development of RFID technology in the supply chain market place. Based on the goals and the implementation phases expected of this plan, we believe that 13.56 MHz ba….[1/10/2004] White Paper on Eliminating medical errors with RFID technology. This paper discusses how RFID technology can help eliminate medication errors: Ensuring data integrity in RFID labels; RFID labels on medications, in syringes, bottles, and other packages; RFID on staff and patients; RFID helps HIPPA compliance; Posi….[11/2/2003]
White Paper on Eliminating medical errors with RFID technology. This paper discusses how RFID technology can help eliminate medication errors: Ensuring data integrity in RFID labels; RFID labels on medications, in syringes, bottles, and other packages; RFID on staff and patients; RFID helps HIPPA compliance; Posi….[11/2/2003] White Paper on Reliability and Costs of RFID Inlets and Labels.This paper discusses the following aspects of RFID inlets and tags: Comparative performance analysis on tags made with etched copper, vacuum deposited aluminum, printed silver ink, and other means of antenna trace formation; The impact of soldered, compr….[9/2/2003]
White Paper on Reliability and Costs of RFID Inlets and Labels.This paper discusses the following aspects of RFID inlets and tags: Comparative performance analysis on tags made with etched copper, vacuum deposited aluminum, printed silver ink, and other means of antenna trace formation; The impact of soldered, compr….[9/2/2003]
The Most Recent White Papers or Reports on RFID
SECURE CARGO CONTAINER AND SUPPLY CHAIN MANAGEMENT BASED ON REAL-TIME END-TO-END VISIBILITY AND INTRUSION MONITORING
The Challenge of Supply Chain
“Needle-in-a-haystack” is a common and deeply felt syndrome challenging security professionals trying to isolate specific problem containers from the more than 21,000 containers arriving daily at US ports and the millions arriving worldwide yearly. Disruption of shipping and trade caused by potential weapons of mass destruction (WMD) using containers as a Trojan horse is one scenario that hounds all experts in custom and homeland security.
Many solutions based on smart locks and seals have been examined and extensively tested since 9/11 [1,2,3,4,5,6,7,8,9]. Most of the current proposed solutions focus on the electronic lock, seal and gasket sensor on the container door. These solutions do not address the problem of intrusion through other surfaces of the containers not touching the lock and seal or gasket nor do they address alteration to the contents stuffed inside the containers [10,11,12]. Table 1 (below) is a list of the basic challenges and the desired solutions.
| TABLE 1: SUPPLY CHAIN SECURITY CHALLENGES | |
| Challenges | Solutions |
| Impossible to inspect all of the containers or even 10%. |
|
| No way to know if tampering occurs during transit and too late to prevent loss upon arrival at unloading port. |
|
| Cannot be sure whether any contents may contain weapons of mass destruction (WMD) |
Using intelligence and automated information to identity and target high-risk containers; Pre-screening those containers identified as high-risk, at the port of departure, before they arrive at U.S. ports; Using detection technology to quickly pre-screen high-risk containers; and Using smarter, tamper evident containers.
|
Considerations for an Effective Intrusion Detection Solution
A “smart box or smart container” foretelling the presence of WMD inside a container is a dream solution. Almost all the proposed solutions for smart containers are based on securing the locking mechanism by monitoring tampering (usually by breakage) of part of the RFID seal. Some monitor the tie-string of the seal while others measure the breakage of the lock-pin or other integral parts of the seal. GE (with partnership of Allset) monitors the change of pressure on the gasket on the door seal [5] and has now added additional sensors.
These currently proposed solutions assume that intruders will get inside the container to take valuables or place WMD in the container by getting in through the door. By tampering with the door lock seal or the gasket pressure, the intrusion will be detected. However, as pointed out by many seasoned professionals [9,10,11,12], “Seals and e-seals detect tampering with a seal, but not container intrusion—despite some manufacturers’ marketing claims” [13]. Monitoring the door seal is only meaningful if the intruder comes in through the front door. It will serve no useful function if intrusion is made through other surfaces of the container, such as cutting through a steel wall or floor panel.
Experts in the field want a solution that places monitoring devices inside the container capable of detecting actual intrusion through any surface by any means. The following table lists some possible physical means to achieve internal detection and possible defeating mechanisms. A new approach to manage this complex problem is also proposed.
| TABLE 2: POSSIBLE INTERNAL CONTAINER INTRUSION MONITORING MECHANISMS AND RELATED PROBLEMS | ||
| MECHANISM | BENEFITS & SHORT-COMINGS | POSSIBLE DEFEATING MEANS |
| Light |
| Intruder can perform intrusion without light. |
| IR or Heat sensor |
| IR is not present if only WMD objects are introduced. |
| Air Pressure |
| Pressure can be monitored and compensated easily. |
| Sound |
| Too many possible noises that can induce false alarms. |
| CO2 or other gases |
| Intruder can use self-contained breathing device. |
| AVANTE RFID ZONER™ method |
|
|
AVANTE developed the patent-pending method of using individual ZONER™ tags each emitting its own discrete power signal. A planned network of RELAYER™ devices is used to provide automatic monitoring and real-time intrusion reporting. The testing done so far is extremely effective with inherent usage costs lower than all other proposed current solutions. Actual intrusion monitoring into the container is now possible. With suitable tracking and monitoring infrastructure, a secure supply chain with end-to-end visibility can be achieved with nominal costs of less than $50 per container. This cost includes hardware and the cost of distribution, management and monitoring services. Efficiencies achieved through use of RFID tagging are estimated at $400-$1600 per container which easily absorbs the costs associated with tagging the container [14, 15].
Finding out intrusion or tampering at the unloading port is much too late!
Most earlier e-seal proposals focused on ascertaining whether containers arriving at US ports had been tampered with or had intrusion through the access door of the container. The monitoring network and readers are positioned at unloading ports such as Tacoma Seaport. Not only is this monitoring possibly not effective, it is also too late.

Figure 1 (above) is an illustration of how some of the earlier e-seals were checked [3]. Since items are checked at a border or a container port, discovery of tampering or the presence of any malicious materials, such as weapons of mass destruction, is much too late. An effective solution should give the ability to inspect any exception or potential tampering in international waters or other locations that will minimize potential destruction or damages [16]. Such solutions will require the ability to provide real-time reporting from monitoring systems as the tampering or intrusion happens. The destination custom and port authorities will have the option to inspect the container and ship away from the seaport. If the carrier is trustworthy, the captain and security staff may be asked to inspect and report their findings that could possibly include a video feed for monitoring purposes.
End-to-end monitoring helps minimize risks
Most plans for securing the supply chain include the use of secure stuffing locations that are monitored by trusted agents and US custom staff. Stuffing and monitoring the contents being placed into containers coming to the US is one of the best approaches. However, the security monitoring of inland transport is the single weakest link in the end-to-end process. Using ZONER™ RFID tags equipped with optional radioactive-chemical-biological sensors placed inside the container, along with an exterior mounted monitoring RELAYER™, creates a cost effective solution providing end-to–end tracking and monitoring after container stuffing.

Figure 2 (above) is a solution that may be used for containers during the inland transit from domestic or foreign stuffing sites or factories.
The ability to sort out containers stuffed with WMD before loading onto an ocean carrier represents a major cost effective step in securing the supply chain. The side benefit is the ability to minimize the stolen goods or possible smuggling activities.
End-to-end visibility and security management of the containerized supply chain should cover all phases of container movements:
In addition to monitoring the stuffing and inland transport of containers, continual tracking and monitoring of the containers based on various operational and storage stations must be vigilantly maintained.

Figure 3 (above) illustrates a cost effective way to monitor both stuffed and empty containers while parked inside a container yard or loading terminal.
A ship sailing to United States may pass through and stop at as many as 17 ports before arrival. Intrusion could occur while at sea or during stops at other ports.

Representing a cost effective solution, Figure 4 (above) is an illustration of using ZONER™ RFID placed inside the container along with the RFID RELAYER™ monitoring network.
Container Real-Time Locating and Monitoring (RTLM) System- AVANTE CONTAINER-TRAKKER™ Solution
The following is an outline and description of CONTAINER-TRAKKER™ container and supply chain security management system with 100% end-to-end visibility:
- A set of RFID ZONER™ tags transmit messages from inside the container. The receipt RSSI changes over time of a few cycles (AVANTE patent-pending) and positively identifies tampering into the container after it has been sealed. The differential signal levels rather than perfect on/off signals minimize false alarms of tampering. Built-in redundancy also helps to prevent false positive and insider tampering.
- All personnel are required to wear ZONER™ RFID badges that are also monitored and recorded by the embedded RELAYER™ RFID reader.
- A fixed site network of RELAYER™ RFID monitors directly communicates with the RELAYER™ reader on the container. Messages from ZONER™ RFID tags inside the container are monitored during both normal and tamper evident conditions. Exceptions and tampering are reported in real-time.
- A monitoring and communication computer is housed in a sealed, hardened tamper proof box. This sealed monitoring data and communication “GREEN BOX” is installed by a third party agency to provide true independent reporting and monitoring services.
- The “GREEN BOX” includes the following sub-systems:
- A redundant processor and non-volatile memory.
- A GPS location reporting system.
- A satellite or other suitable communication means.
- An optional, multi-channel video digital recording device. Video feeds to destination authorities and independent monitoring agencies are made when possible.
- A trusted organization, “Public Independent Monitoring Agency (PIMA),” is chartered to provide the services of receiving all data and providing visibility throughout the end-to-end transportation process. AVANTE proposes PIMA as a network of companies certified by the World Trade Organization located in the partnering countries. The cost for such monitoring services would be paid in part from the fixed container fees paid by shippers.
A cost effective method to foretell the presence of WMD inside the container and the ability to detect intrusion is only the beginning of any security solution. For a secure supply chain management, the system must achieve all four aspects in the Secure Container Initiatives (See TABLE 1).
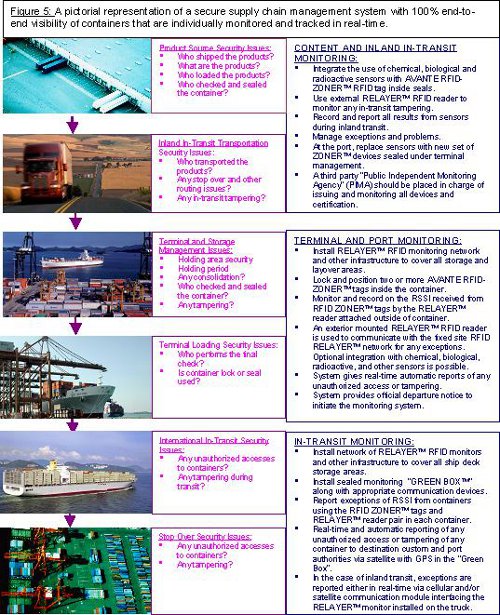
The flow illustration in Figure 5 (above) lists the issues and processes that must be resolved to ensure international supply chain security. A secure supply chain cannot be achieved without technology including detailed process monitoring managed by trained organizations and people among the partnering countries.
A solution for container and supply chain security and visibility must include a functional real-time monitoring infrastructure and services network
Chris Koch, President of the World Shipping Council once said about the e-seal “smart box” project (now working for GE), “This is a shipper-applied device. Customs will do the reading of the device. I don’t think these particular containers will receive expedited treatment.” (Journal of Commerce Online, November 19, 2003) The “smart container” solution should not entail only the placement of e-seal devices on container doors. The solution must include trusted agents in deploying and placing devices and then monitoring the processes and data from end-to-end.
A network of trusted monitoring clearing houses of the supply chain data must be established. Also a network of trusted local agents is required to distribute and properly install the monitoring ZONER™ and RELAYER™ devices.
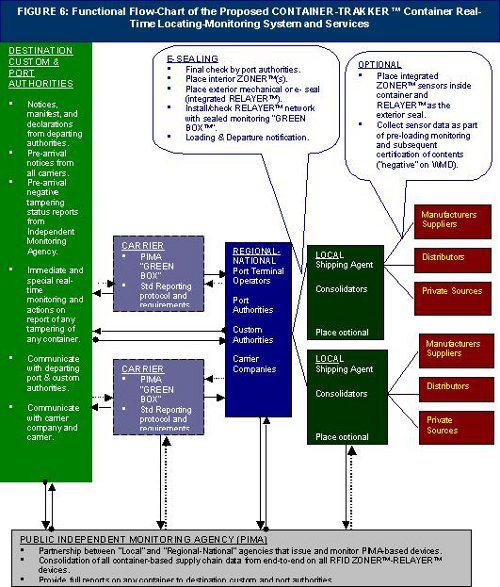
A suitable workflow representing the solution is shown in Figure 6 (above).
Real-Time Locating & Monitoring (RTLM) Container and Supply Chain Services
While technology may be the building block of a cost effective solution, securing the world trade and supply chain is a complex integration of technologies, effective processes and the proper execution of protocol by trained people. The technology of a “smart box” or “smart container” must be coupled with end-to-end monitoring and tracking systems and services to provide visibility and security.
A full solution as depicted in Figure 6 is best met with partnerships between government agencies, existing terminal operators and supply logistic management companies. The following is some of the proposed functions of this system.
- 100 percent, 24/7 real-time monitoring and reporting of all access to containers after sealing from departing ports.
- All status and exception reports are made independently of onboard and operational staff.
- Exception and tampering reports are made in real-time. Normal status reports are made periodically as scheduled.
- Reports of exception and tampering are made in accordance to the following harm-benefit protocol:
- First to the destination port and custom authorities.
- The same reports are sent to the Public Independent Monitoring Agency (PIMA) as the information clearing- house.
- The destination authorities will manage any exception events and communicate with the departing authorities and onboard security staff. No direct reporting of events will be made to the onboard and departing authorities unless authorized by the destination authorities or, by mutual or international agreement.
- The monitoring devices inside the containers, the message-relaying network onboard the carrier and the communication network are installed and monitored independently by a third party independent agency.
- AVANTE Container ZONER™-REALAYER™ container tracking services include self-diagnostic reporting along with system event and periodic reporting.
- Additional real-time video feed triggered by tampering is an available option.
- All systems are built-in with redundancy to prevent false reporting.
- This end-to-end container visibility provides security equivalent to 100% inspection of all containers.
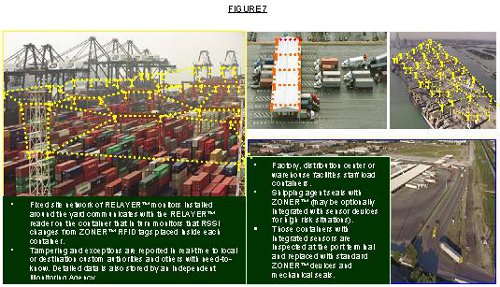
Figure 7 (above) is an illustration of RELAYER™ RFID reader network placed at a port terminal, truck terminal, container port or distribution center for stuffing containers.
Managing false alarms in e-seal
One of the problems preventing the e-seal technology from gaining faster acceptance is the high rate of false alarms associated with the technology. Opinions differ but a false alarm rate from 1% to 0.01% seems to be acceptable. AVANTE, however, believes false positives must be kept below 0.01%. This can be achieved through the use of two or more active tags emitting with large RSSI differentials along with other sensors and logistics. While the use of quantitative signal differential is effective even for a single ZONER RFID tag, any vibration may distort the door seal to cause a fluctuation of power signals being received by the monitoring RELAYER™ RFID reader. The use of two active ZONER™ RFID tags provides additional safety to avoid false alarms caused by any fluctuation.

Figure 8 (above) is a representation of the user interface testing discrete signals received by an outside monitoring network.
Conclusion
Container and supply chain security is an urgent concern for the international community. A temporary shut down of US ports would have a chilling effect on economies all around the world. E-seal security capabilities on lock and seal cannot address intrusion through anything other than the container door and certainly not through any of the containers’ other surfaces.
A special ZONER™ RFID technology that allows quantitative measurement of differential received signal strengths by embedded RELAYER™ RFID reader outside of each container has been developed by AVANTE. ZONER™ RFID Tags with suitable sensors are placed inside the container to monitor intrusion on any surface of the container, not just the door. Each of the RELAYER™ RFID readers also records and reports all personnel wearing ZONER™ RFID badges that handle the container along the transit.
An end-to-end tracking and monitoring system solution based on patented RFID sensor technology is presented to provide secure supply chain management with real-time visibility. The long-sought solution of a “smart box” or “smart container,” endorsed by custom authorities, can be achieved without the excessive false positives that plague traditional e-seal technology.
The cost of less than $50 per container in implementing the “smart container” initiatives can be paid for by the $400-$1600 cost savings achieved by shippers and their partners resulting from supply chain efficiencies and loss prevention.
REFERENCES
- “Electronic Cargo Seals: Context, Technologies, And Marketplace”, Michael Wolfe, July 12, 2002 (Prepared for ITS Joint Program Office, Federal Highway Administration, and USDOT).
- “Report on Electronic Container Seal Technologies (Task 2)”, Chel Stromgren, August 23, 2002. (Funded by the Center for Commercial Deployment of Transportation Technologies at Cal State, Long Beach).
- “Part 1: Electronic Container Seals Evaluation”, Mark Jensen, December 2002 (Sponsored by USDOT ITS Joint Program Office, Office of Intermodalism, FHWA Office of Freight Management and Operations).
- “Securing the Supply Chain: Container Security and Sea Trial Demonstration Results”, RAE Systems, Jan. 2005.
- “GE Uses RFID to Secure Cargo”, Jonathan Collins, RFID Journal, January 12, 2005.
- “High-Tech Container Solutions, www.frontlinetoday.com
- “Mesh Radio Network Performance in Cargo Container”, Sensors March 2005.
- “Container Security: Expansion of Key Customs Programs Will Require Greater Attention to Critical Success Factors; GAO-03-770, July 2003 Report to Congressional Requests.
- “Security: Improving the Security of the Global Sea-Container Shipping System”, Maarten van de Voort, Kevin A. O’Brien with Adnam Rahman and Lorenzo Valeri, 2003 Rand.
- “The Limitations of the Current Cargo Container Targeting”, March 31, 2004, Written Testimony by Stephen Flynn, Subcommittee on Oversight and Investigations, Committee on Energy and Commerce, US House of Representative.
- “Operation Safe Commerce Phase III”, US DHS RFP, Due February 18, 2005.
- “In-Transit Container Security Enhancement”, World Shipping Council, International Mass Retail Association, The National Industrial Transportation League, September 9, 2003.
- “It is important to recognize that e-seals are not necessarily a solution to containerized cargo security concerns.” As a report by the Vulnerability Assessment Team at Los Alamos National Laboratory states. ”High-tech electronic seals are not automatically better than simple mechanical seals, and are often worse.” “Tampering-Indicating Seals: Practices, Problems and Standards”, by Roger G Johnston, Ph.D., Vulnerability Assessment Team. Los Alamos National Laboratory, Los Alamos, New Mexico. Prepared for the World Customs Organization Task Force on Security and Trade Facilitation February 2003 Meeting, Page 1.
- “Smart” Container Success Will Depend on Government Mandates”, Feb 1, 2005, Frontline Solutions.
- “Frequently Asked Questions, Attachment A (End of the article posted in www.avantetech.com).
